The Best Laptop For Hacking in 2024 (Cyber Security) – Guide & Tips
Intros out the way. Let’s get to the point .
The best laptop for hacking does not need to look like this:

It doesn’t have to be powerful and it doesn’t need to look cool. Nor do you need antennas sticking out or a skull stricker on the back cover.
Why is this post titled Cyber Security?
Because the concepts of black hat malicious and criminal hacking are also applied in white hat hacking & penetration testing.
The difference is that people who study the latter (or at least label themselves as the latter…lol) are hired by companies to find and fix security gaps in their systems and networks. They’re also hired to catch and stop malicious hackers like you.
Obviously, I cannot write a post encouraging you to become a malicious hacker.
So by learning about cyber security you’ll also learn how to become a hacker (hopefully a good hacker).
What else will you find in this post?
I’m assuming everyone reading this is a complete beginner to hacking. So I’ll introduce some basics while at the same time introduce you to the hardware needed for hacking.
But as you’ll find out soon it’s not so much about hardware.
If fact you can do some serious hacking even with a rasberry pie.
No, it’s not something you eat. It’s a computer (shown below).

The tiniest computer. Mostly used for programming testing/practice in engineering.
The point is…it doesn’t matter what computer or laptop you use.
However…
That doesn’t mean good hardware is useless. Of course it helps! Some scripts will run faster with a dedicated GPU with lots of cores for example and reduce the time it takes to get a password from weeks to minutes.
Before we keep going, let me clarify something:
Use the information here to hack into computers that you’ve been given the green flag for. This is called ‘ethical hacking’. You can later on use all this knowledge to work against criminal hackers as a penn tester or as someone in the cyber security business(awesome salaries in 2024 btw).
Best Laptop Specs for Hacking
Before I talk about the hardware, let’s summarize the ‘apps’ and ‘tasks’ a hacker or a penn-tester uses/does. This will help you understand why I’m favoring a piece of hardware more than others. I’ll be brief here but you can check the last section for more details, tips and helpful links.
1. Virtual machines: They use Windows + Kali Linux and this is what your set up should be first. This doesn’t require much RAM or CPU. However, nested networks (virtual machines on top of virtual machines) or several VMs at once for simulation purposes requires lots of RAM & CPU cores.
2. Programming Languages: This doesn’t require good hardware but SSD+extra RAM is very handy. Also, it’s always better to pick a machine that can FULLY support Linux.
WiFi 6 or latest: will have compatibility with the most recent WiFi Protocols plus backward compatibility with the older protocols , super useful to target different networks like your neighbor’s WEP secured network *cough* I mean to test his network for vulnerabilities with his consent.
Using a mouse gives you more speed for tracking bugs and interacting with the OS (yours or your target) . Trackpads are too slow.
Storage(Optional)
Even if you’re saving tons of hacker software and scripts, 128GB will last you a lifetime.
Be sure your storage is either an SSD or any of its fast variants (eMMC, Flash) as it will make Virtual Machines snappy and they won’t make you wait (unlike the spinning needle hard drives) to run your hacking scripts and finish your hackery.
These laptops are NOT special. You can find laptops with simila specs at your near computer store.
Linux is not installed on these, you will have to do the installation yourself.
How are these laptops special then?
they’re simply good deals for those in the US and have a solid built & well designed cooling so they’ll last you longer than the average laptop.
All of them have the hardware to run all programming languages hackers use and also they can run several Virtual Machines so you can practice your hackery on it too (you’ll be simulating networks to hack into with different operating systems and different layers of security).
Laptop # 5: has too much hardware for hacking (probably unncessary) since it’s a gaming laptop nonetheless it’s useful if you ALREADY know how to write/run password cracking scripts (it’ll finish the job several of orders of magnitude faster than most laptops) . They’re also useful to run AAA games for which you can write cheat codes/scripts too. It’s very very expensive but it’s listed there mostly for information purposes. We’ll keep talking about hacking as we review each laptop.
1. Acer Aspire 3
Cheap Laptop for Hacking

AMD Ryzen 5 7520U
8GB DDR5
AMD Radeon 610M
512GB SSD
15” full HD IPS
3.92 lbs
10 hours
WiF 6 802.11AX
Windows 11Home
This is a very basic laptop nonetheless it’s got the hardware you need to even start testing labs and run a few VMs.
RAM: 8GB DDR4
This is because it’s got 8GB RAM and it’s upgradeable. You can take it apart , buy an additional RAM stick for 10 bucks, and make it 16GB RAM. I have a tutorial on how to do this here though with a different laptop the process is the same.
Though you won’t need that when you start. For now 8GB RAM will do as this as much as you need to start programming (this requires the use of IDEs) and to launch Kali Linux (the distro most popularly used for hacking).
If you do get good at programming and want to write your own scripts down the line, that won’t require any special hardware either. As long as you have 8GB RAM, a decent CPU + latest WiFi protocol, you’ll maximize your chances to crack down passwords.
GPU: AMD Radeon 610M
However, cracking passwords with scripts (from the internet or your own) will take a lot of time if you don’t have a dedicated graphics. But again if you are not interested in these password cracking scripts but rather ‘hacking’ into systems this laptop will do.
| Acer Aspire 3 | |
| PROS | CONS |
|
|
2. Lenovo Ideapad 1
Budget Laptop For Hacking
 AMD Ryzen 3 7320U
AMD Ryzen 3 7320U
8GB DDR5
AMD Radeon 610M
512GB SSD
15” full HD IPS
3.48 lbs
8 hours
WiFi 6
Backlit + Fingerprint Scanner
Windows 11 Home
This Lenovo Laptop has a wekaer CPU (Ryzen 3 vs Ryzen 5) but it’s from the same generation and as far as hacking is concerned this is fine for tasks like:
- Running one/two VMs
- Programming
- Running CPU dependent scripts
- Installing Kali Linux natively
I’ll explain a bit on the latter but let me say that this laptop won’t be a great one for simulating networks because the lack of CPU power limits the number of virtual machines to just a few.
Nonetheless for all other purposes, this is fine so if you’re a beginner you aren’t likely to run simulations of networks just yet (probably take you a year or two if you work hard). I mean you can but you’re not going to have the skills just yet to benefit from those simulations. You still need to learn programming and how to use Kali Linux for which this laptop is perfectly capable of.
Linux: Hardware Compatibility
Assuming you’re quiet advanced with Linux and you want to install Linux natively on this machine (ditching Windows altogether or just leaving it as ‘second’ boot system , that is when you restart you choose the computer to run either) …then this Lenovo is more ‘compatible’ with Linux. What I mean is that the hardware from the Wifi Card to the sound speakers wiill work flawlessly when Linux is installed natively (without Virtual machines). This isn’t the case for all laptops though most can fully support Linux when you buy Lenovo you increase the chances of every piece of hardware working correctly.
GPU: AMD Radeon 610M vs Intel Xe Graphics
Here’s the thing…with these two GPUs.
This laptop has the same AMD Radeon 610M the Acer has, it’s a weak GPU, no need to sugar coat it. While shopping for cheap laptops for hacking like this model (8GB RAM + recent CPU) you’ll also come across the 12 or 13th gen Intel Core models with the Intel Xe Graphics card.
Both of them do add a performance boost when you’re running a script for password cracking since these two also have ‘cores’ the script can work with. However, Ideally you want a graphics card like the 4050RTX which has more powerful and numerous cores. If you’re also planning to get into data analysis, AI scripts and machine learning, it’d be best for you to find a laptop with a dedicated graphics and not this model.
| Lenovo Ideapad 1 | |
| PROS | CONS |
|
|
3. Lenovo ThinkPad T16
Best Lenovo Laptop For Hacking
Intel Core i7-1355U
32GB RAM DDR5 (Upgradeable to 48GB)
Intel Iris Xe Graphics
1TB PCIe NVMe M.2 SSD
16” FHD IPS 300 nits
3.7 lbs
10 hours
Windows 11 Pro
WiFi 6
Linux: Best Compatibility
While the Lenovo above was hardware compatible with Linux. If we are talking about the most IDEAL laptop that will never get you ANY compatibility issues with Linux (natively installed) are (as far I am concerned) two: They are the dell XPS and the Lenovo ThinkPad T series. Obviously, there are MORE laptops that have the BEST compatibility but these are the two that I know of.
A common problem with laptops (when Linux is installed) is the WiFi Card/TrackPad or any small accessory like fingerprint readers that do not work once linux is installed, this is due to lack of drivers being developed by the Linux community for that specific’s model hardware. But since most hackers , programmers use ThinkPads these are the first ones to be taken care of by Linux developers. You will get ZERO issues with Ubuntu with either of these.
Hardware Customization
Now this model is expensive and thats because it’s kind of maxed out in terms of CPU and RAM. It has the latest most powerful Core i7 (for non gaming/3D or creative media purposes) and also has 32GB of RAM. This is completely useful for recreating network labs and start testing your hackery skills or scripts.
But if you still want a thinkpad as a beginner you can go for the thinkpads that have the Core i5 or Ryzen 5 with just 8GB RAM.
Penn testing: if you’re going to sign up for penn-testing school or a course on penn-testing you’ll be working right away with networks labs & virtual machines to make them thus it may be a good idea to use this model and if needed upgrade RAM to 48GB RAM later, you could also upgrade storage later. Also if you’re choosing another model (you don’t want/need the Linux compatibility) then remember to choose a CPU with just as many if not more cores (if you have the budget): More Cores = more complex networks = better simulations.
| Lenovo Thinkpad T16 | |
| PROS | CONS |
|
|
4. Lenovo ThinkPad E16

Best Laptop For Hacking
AMD Ryzen 5 7530U
24GB RAM
AMD Radeon 610M
1TB PCIe NVMe SSD
mdi-icon name=”monitor” size=”2x” color=”black”] 15.6″ 1920×1200 (WUXGA)
4.34lbs
10 hours
Wifi 6 802.11AX
There are many alternative cheaper Thinkpads if you want the best compatibility for Linux but this is my favorite: a thinkpad from the E series.
You can find ThinkPads from the E-series even cheaper, the cheapest ones will have 8GB RAM but adding more RAM doesn’t increase the wholesale price significantly so you might as well buy it with more RAM & Storage out of the box.
All of these come with TWO ram slots and they usually have 16GB soldered which means you can only add an additional stick or replace it with another RAM stick.
This model for example has 24GB: 16GB RAM (soldered) with 8GB RAM (replaeable), you can add 16GB RAM to make it a total of 40GB. Again only do the upgrade if you’re running penn testing labs (through VMs).
CPU here is the latest Ryzen 5 and again CPU doesn’t matter much unles you want to run several virtual machines. Cracking WPA2/PSA encrypted data will entirely depend on having dedicated graphics card.
| Lenovo Thinkpad E16 | |
| PROS | CONS |
|
|
5. Razer Blade 16
Best Laptop Computer For Hacking

Intel Core i9-14900HX
64GB RAM
NVIDIA GeForce RTX 4090
4TB SSD
15.6″ Dual-Mode Mini LED (UHD+ & FHD+)
5.4 lbs
2 hours
Wifi 7

This is the kind of hardware you want if you’re planning to write and run scripts for password cracking and hacking into networks wirelessly. It’s mostly really about the GPU because it has literally almost 10 000 cores. It’s also super useful if you want to use parallel processing scripts for other purposes as in Data Science & Machine learning.
Testing Labs:
Of course gaming laptops like this model also get you maximum amount of RAM & Threads & even better storage set up for you to run nested works and pen testing labs with lots lots of virtual machines. This is where the Core i9 comes in handy, Virtual machines RUN on CPU cores not on GPU cores. Since this one has 32 threads and each thread can support 2 VMs (maximum on iddle) then you can run about 30 * 2 = 60 VMs . 2 threads are reserved for the host.
| Razer Blade 16 | |
| PROS | CONS |
|
|
Warning: Read Before Checking Next Section
So please get nto ethical hacking instead. You’ll learn all the tricks and schemes hackers use and still be able to get a high paying job through penn testing or security.
Hacking: Software & Hardware Guide
The information presented here is from those years attending hacking conferences and hacking thereafter as a hobby.
These conferences were ethical hacking talks. Hackers do not gather and promote hackery at public conferences. That would get everyone under investigation.
I assume most people reading this barely know how to write a piece of code so to make it much easier I’ll divide this section in three parts:
- Types of hackers
- Software for hackers
- Hardware for hacking
1. Types of Hackers
True hackers understand how entire computer networks work:
What’s a stack, what’s a heap? What are Architectures? What’s an assembler? How do network protocols work? What are their weakness/strenghts?
If you understand and know how to take advantage of this knowledge, you will be quick and prone to find vulnerabilities in a network then hack it.
Real hackers don’t need fancy software for this.
They can do all of this just by looking at code. That’s right, just by looking at code they can tell how the network traffic works and how the applications in it work too as shown below:

You don’t need a super computer to look a code. We all know a cheap laptop with 8GB RAM will let you write, edit and see code. That’s why I emphasize learning how to code for a few years instead of trying to download software from the internet to hack into networks.
Linux: A must for all hackers
Chances are, even that cheap old laptop sitting in your grandmas basement will work just as good as Link’s computers if you install Linux which you have to learn anyways. No way around it…that’s because:
-
Linux is one of the most lightweight OS systems. Some distros (versions of Linux so to speak) are known to run even better on very old cheap hardware.
- Distros are basically different versions of Linux tailored for a specific purpose.
-
Linux is mostl used due to all the programming languages natively installed on Linux and all the packages, resources available for Linux users.
- The terminal is a MUST use from the very first day though getting acquianted may take a few weeks.
-
Linux provides complete control over hardware and network ports. Unlike Windows or OSX where you have limited control you can do whatever you want (through applications/Linux) with your hardware.
- This means if you know what you’re doing (with ports & networks), you can make it VERY hard for your system to be hacked.
Now we’ll go over the three types of hackers!
SCRIPT KIDDIE
If you’re still at the script kiddie level you only need a machine to run a version of Linux. Usually Kali or BackBox Linux. Any machine can run these distros.
Script kiddies don’t do anything original they barely know how to code. If you want to stay at this level you don’t need to worry about display, keyboard because you won’t be makign these scripts yourself. You’ll just get them off fiver for 5 bucks most likely.
Unfortunately you’ll get caught very quickly if you remain at this level.
If you don’t want to rely on someone else’s scripts/exploits. Then start with learning how to code for a few years, learn how to use Linux, OSX and UNIX SYSTEMs. Of course you need to learn how Windows works and I’m not talking about how to use them. I’m talking about how an operating system works.
After that you want to learn networking and get into security layers.
You can then learn how to write your own scripts.
Once you write your own scripts, try to learn cryptography and every other ‘advanced’ topic in computer science pertaining HACKERY.
Advanced Programmer (Almost Hacker)

If you’re an computer engineer, you already have most of the skills you need.
In fact, most hackers are computer science students or engineers.
They quit their jobs and start playing around with operating systems and networks first. Then they start developing new modules for metrasploits which qualifies as hacking.
Once they’re able to make their own metrasploits, they can finally move on to making virus , worms, browser exploits, email client buffers, etc.
A good grasp of a large selection of programming languages is needed to make these . There’s no need for a big machine to make these scripts/programs. They’ll just need an IDE to code with and run a virtual machine for Kali Linux. Only an 8GB RAM laptop is required.
After they make their own exploits, the next step is to simulate a local web server (the host) to test malicious code.
In this scenario, a couple of virtual machines is best to simulate several target OSs.
If they are succesful, they stop after the ‘testing part’ otherwise they’ll be stepping in criminal hackery.
Stealthy Real Rogue Hacker

These guys no longer target small networks but rather large corporations and institutions and even dare to target servers from the government.
If you want to spot these types of hackers within your company, know the following:
They usually disguise themselves as employees.
This is the easiest way for these hackers to hack a company. They try to get one of the typical laptop issued to employees. They will go after an used laptop to avoid people coming up to them trying to be helpful because he is the “new employee”. That and anything else that will help their camouflage.
But they also bring their own laptop which is most of the time thin (not bulky not heavy) because these machines must be connected to the network overnight to try and hack it while being hidden inside a stack of papers.
When going into full attack mode, they will run either Tails or Kali . These distros can run out of a USB drive which once unplugged deletes every trace/data/evidence from the computer that was used for hackery.
The best hackers in the world can even use a tiny USB computer or raspeberry Pi which is manually injected into a network or server and then have all the data (and passwords) just flow into their rig back in their base.
Anonymous doesn’t need to do that though he has to resort to more ‘safe’ schemes which is basically remote accessing their targets through code.
2. Software
Operating System: Not Windows!
During the first hacking conference I attended. There was a problem with the projector and the presenter asked the audience if anyone had a Windows laptop he could borrow to run the presentation.
There was no one in that huge crowed running anything but Mac OSX or a Linux Distro.
Many people started commenting on how innappropiate was for someone like him (supposedly an ex-hacker) to ask such question. One person even stood up and called him out saying he was obviously spending way too much time with the layman and business people rather than penn-testers or hackers.
He then proceded to clarify that he had Mac OSX, Linux OSX and Windows 7 rigs back home but he decided to bring this time his two-goody shoes Windows laptop to the conference for obvious reasons.
Everyone laughed!
Why Linux?
It basically comes down to being a very flexible operating system.
In other words, you can do whatever you want with it and the fact that it’s open source means you can tailor the Operating System to look and operate as you’d like.
Like OSX (mac) , it’s also a hybrid OS, which basically means it has both a command line interface (terminal) and a graphical user interface for you run code.
You can use either to fully operate the system to your liking. It also gives you full control of all the hardware in your computer.
Now hackers will usually make their own Linux Distro (anonymous) but you don’t need to do this . There are HUNDERDS of readily to install Linux Distros with hacking and penn testing in mind. They even have preinstalled software and languages for these purposes.
Here’s a run down of the most popular “hacking” Linux Distros:
The most popular distro for pen-testing. Developed by Offensive Security as a re-write of BackTrack many many many years ago and it still tops the list of all operating systems used for (ethical) hacking.
Not the best distro if you’re a newbie.
The community is filled with advanced hackers so you’ll be vulnerable to attacks. Unless you know what you’re doing and know your way in and out of the OS, it will backfire on you eventually and even attack vector will succesfully hack your system.
Someone who knows how to use Kali Linux will easily hack someone who only has a few months using it.
Tails
For illegal tools like NMAP , most hackers install a Distro like Tails. This is because Tails has best degree of anonymity super important when going in Live Mode.
Cybor Hawk
This is a great alternative to Kali Linux. It’s mainly used for penn testing . Unlike Kali, it has an amazing GUI which makes configuring any rig much much easier. Highly recommended for newbies.
This is a Debian-based distro developed by Frozen Box’s team. It’s popular for pen testing, computer forensics, cryptography. In other words, ethical hacking.
BackBox is an Ubuntu-based Linux Distro mainly used for security assessment and penn testing.
A live Linux environment pre-configured for penn testing work especially web based penn testing.
Other popular distros with very strong points in their own right are:
- Pentoo Linux
- DEFT Linux
- Caine Linux
What about the software specifically designed for hacking facebook accounts, cracking WEP Wifi Passwords and so on?
I can’t link any malicious software here because I will get into trouble myself.
If you google long enough you can find LOTS.
For study purposes, you should look at them as scripts instead of software. Basically try to see them as nothing more than lots of lines of codes that outline a sequence of steps that activate and/or control a wide variety of computer processes to hack a target. Download them, open the files in an IDE or notepad and try to understand the code and go back to it as you learn more and more about programming and hacking.
They go by the name of:
- Virus/worms. Do not click the link unless you have an antivirus.
- Browser Exploits: Don’t click the link unless you want your entire browsing history published on facebook/reddit. Jk.
- Email client buffer exploits: Don’t click here if you want everything on your email exposed to the web. :’)
3. Hardware for Hacking
There are basically four types of hacking or practice hacking:
1. If you are going to hack into computer networks/systems using the internet.
You need a system that can support a hacking or pen testing Linux distro (Kali Linux).
It’s proably better even if find a system that lets you access the BIOS to let you boot your own Operating system through an external drive (USB or CD) and supports drivers for integrated devices.
This means virtually every laptop that supports the home or professional version of Windows. You will have issues with all other operating systems natively found on new laptops.
MacBooks are also good after you go through the painstaking process of installing Linux on them. ChromeBooks are tricky, they may or may not support external devices where you can mount an operating system on it or devices like external wireless cards
2. If you are just going to write code and program ( M A K E scripts)….
This can be done even on a Chromebook. So any operating system works here. This means that pretty much any laptop is good!
In fact, Chromebooks might be the better choice here as they support Chrouton ( Linux Distro for Chrome OS ) which should let you have a full blown Linux environment (the best for programming purposes).
OSX (Mac) is also a better alternatie than Windows because it is a linux variant so you get the same programming environment and access to a terminal just like you would on a Linux system.
3. If you want to simluate networks to hack into, you need to run several virtual machines.
This means having a windows system with as much RAM as you can afford and a CPU depending on how many virtual machines you want to run. I’d say any modern CPU should let you run at least 4 VMs with no issues.
4. If you want to write and run scripts for password cracking & dictionary attacks.
You want a laptop with a GAMING graphics card on it. The more CUDA cores the GPU has, the faster the cracking. We’ll talk more about this in the next section.
Again if you are a newbie just get started with whatever you can get right now even if its a laptop you already have. Even an old cheap laptop with the screen falling off is a good start, once you install Linux on it, it wil lfly and you’ll be able to learn all the basics. for hacking
A) CPU
Writing hacks (Coding):
CPU should be the least of your concerns. Most of the software written for hacking by hackers can run on a raspberry pie.
Virtually every MODERN CPU will have at least 2 cores and more clock speed than you’ll ever need.
You don’t have to go for these CPUs but if you want to run a virtual machine (at least one) or if you want to run Windows 10 Home or Windows 11 you’re going to need a modern CPU that can support 8GB RAM and up to 16GB RAM for more virtual machines. Celeron Pentium Atoms and any other weaker CPU will do fine if you just want to run Linux on your laptop, you will not be able to run Windows 10/11/12 properly with weaker CPUs like Celeron, Pentium and so on.
Hacking Networks(or Pen-Testing):
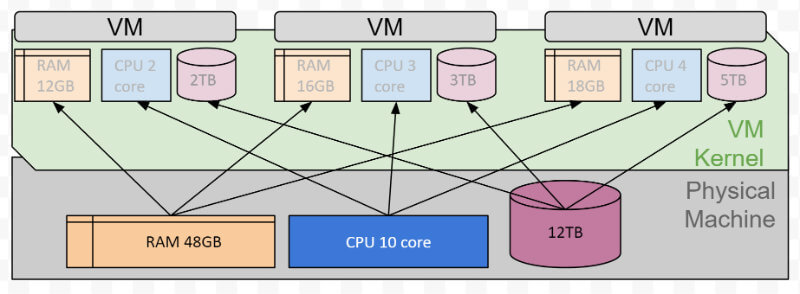
Here you are simulating networks through virtual machines, you might go as far as simulating “nested” networks, that is, having a VM inside a VM.
What you WILL want to buy in the future for this (not now!) is the most powerful CPU you can afford (after you max out on RAM).
By powerful I mean first FOCUS on “number of cores” (actually threads) after you’ve chosen a list of CPUs with the same # of threads, you can focus on clock speed.
Update: note that the 12th and 13th generation Intel Core CPUs have more cores but some of these cores do not support hyperthreading. Basically making each core less efficient for running virtual machines. More information on my post on virtualization. Nonetheless you’ll get about the same number of virtual machines running.
GPU
Brute Force Password cracking:
Cores found on the CPU and the GPUs play a role in making dicitonary attacks/password cracking a lot faster. The more cores you have, the faster the attacks are, the faster the attacks, the faster you’ll get access into your target or get the password.
Now since the GPUs can have up to 10 000 cores (4090RTX) and the CPU only has 16 at the most. For password cracking purposes and any other paralllel processing operation, it is not smart to invest on CPU cores. It is better to entirely focus on the GPU.
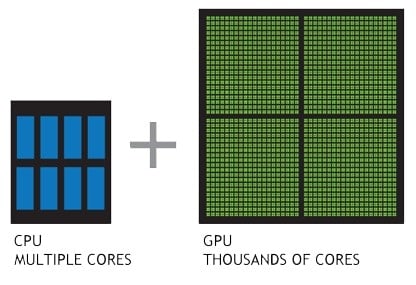
Ex: GPU cores will assist in cracking passwords (mostly WiFi) with WPA2/PSA like encryptions and also run parallel processing scripts (dictionary attacks) much faster.
How is it that the GPU can have so many cores (10 000) and the CPU only up to 16?
CPU cores are built to handle much much complex and a wide variety of data (including graphics). However, GPU cores are designed mainly to run ‘simple’ calculations and graphical data. Thus for simple brute force processing tasks, you don’t need a complex computing processor such as a CPU, a simple processor will do and the more of these you have the better. It’s like asking 3 engineers to change 20 lightbulbs as opposed to ask 20 averge joes to change 20 lightbulbs…which group you think will get the job done faster?
Their usefulness is not limited to password cracking but any programming task or data ‘crunching task that CAN make use of GPU cores. This is called ‘parallel processing’ and the field behind is referred to as parallel programming.
Hackers rarely use their laptop for password cracking purposes though…
It is their last resort. Because it are very risky.
They will instead do the password cracking through SSH . This means remotely using a very powerful desktop with a stack of GPUs.
Most of the time, however, they will offload all password cracking tasks to cloud-based Linux GPU instances which is way way way faster than a desktop or a laptop with a stack of GPUs.
If the software you are using does not work, it probably has to do with the dedicated GPU (NVIDIA) being used by default. The solution is to go to the BIOS and force the BIOS to use the iGPU or just go to the display settings and force the app you’re running to use the iGPU.
RAM
8GB
Hackers are happy with just 8GB RAM. Ethical hackers can do wonders with just 8GB as well.
Mainly because 8GB is enough to run at least ONE VM for Kali Linux to run alongside the host (Windows).
4GB
If you have a windows system (home or professional), 4GB is barely enough RAM to run a windows operating system (10 or 11) and an IDE.
The moment you try to do something else like running a VM for Linux, you will lag.
If you can only afford a system with 4GB RAM, just delete what’s already in the system and install Linux instead, that is delete Windows.
4GB is plenty RAM to run an additional VM on Linux and an IDE and a few more programs.
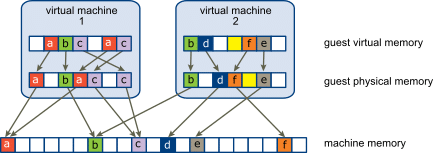
How is a VM useful for hacking?
They’re not only useful for home labs (target simulations) but also because they add a layer of anonymosity and are much much easier to restore (you can save them on a USB drive and restore all your data on another computer).
16GB RAM and More: Only for Pen-Testing
Lastly, for penn-testing purposes, to run security testing on a entire simulated network, you will need to run several virtual machines .
If you’re running 4-5VMs , 16GB RAM should be plenty. As you get closer to 10-15 VMs, you will need at least 32-40GB.
High-end 17 inch gaming and workstation laptops can accomodate 64GB but it is unlikely you’ll ever need this much.
DDR5 vs DDR4: You’ll probably come across different types of RAM. Of course the latest are going to be better because they’ll increase CPU’s performance by feeding data at a much faster pace but the gains are not significant for hacking operations and for launching IDEs or running Virtual Machines. They’re better but not something you would have to obsses over with.
NetWork Card
If you really want to learn all there is to know about ethical hacking and what hackers do, you will need to buy an external wifi receiver (or adapter) that can support packet injection (this is a big part of hacking).
You’re going to use this to run code which will use this adapter to “attack” other WiFi networks.
Dual band or tri band AC network cards (like the latest WiFi AX or the latest WiFi 7) are the best for getting into WEP secured networks quickly but you’re not going to find WEP networks these days. Even your neighbors will use a WiFi network with WPA2 encryption. So nothing is going to be cracked quickly.
Hackers buy something that’s very portable and easy to destroy. They like laptops that can support an additional hard drive and make it easy to remove (to be destroyed later for evidence purposes).
They will NOT install anything on the M.2 Drive (built-in) which is attached to the motherboard for obvious reasons.
They will also switch from one MAC address to another (super easy if you have more than one network connection).
Desktop + Laptop
The vast majority of hackers get a cheap 300 dollar laptop with a lot of battery life like a refurbished MacBook. In fact, the MacBook was the most popular laptop on every convention I have attended, nearly 75% of the auditorium had a MacBook, the other 25% either had a Dell/Lenovo ThinkPad.
Why?
Because they can just SSH into their more powerful rigs back home to access virtual machines and have access to different operating systems
Their desktop rigs are equipped with top of the line GPU and CPUs to do all the cracking/run injection packets and every other type of attack that requires a lot of processing power.
They use their cheap 300$ MacBook to simply write all the scripts/code they will run back home.
It doesn’t necessarily have to be a MacBook….
All you need is a Core i3, a recent integrated GPU and the rest can be spent on extra RAM (this is the cheapest hardware to upgrade – 15$ bucks will get you an extra 4GB RAM).
Then they install a Distro like Kali Linux (or any of the other distros mentioned before , they will all have more or less the same pre-installed software you will use).
Now that’s for ETHICAL HACKERS or those learning how to become a hacker.
Criminals hackers use whatever device they can get their hands on because they have to trash it later for evidence purposes.
Some even go as far as building their own. They design them with enough hardware to do all the stuff they have in mind and make it cheap enough at the same time so that they can be destroyed later for evidence purposes.
Last Comments
For more specialized tasks, you will find yourself looking at FPGA boards or software defined radios, but don’t worry about those things until you deep dive into this field after a year or two.
Anyways, this info is all over the web, not necessarily on the first page of the search engines but it’s still there (you may have to go through the last pages of google).
If you need more info, just look up “Ethical Hacking”.
Even udemy will have a lot of free courses about it.
What you’ll find on youtube though are usually lectures given by guys who got caught and eventually went to jail but worked out a plea deal with the Feds (kind of like the movie “Catch me if you can” ), so they’re definitely teaching all the good stuff.
The same goes to you : unless you’re really good, or really lucky, you will eventually get caught. Study hacking for penn testing purposes instead, lots of money and you can call yourself a hacker too!
Author Profile

- I am physicist and electrical engineer. My knowledge in computer software and hardware stems for my years spent doing research in optics and photonics devices and running simulations through various programming languages. My goal was to work for the quantum computing research team at IBM but Im now working with Astrophysical Simulations through Python. Most of the science related posts are written by me, the rest have different authors but I edited the final versions to fit the site's format.
Latest entries
-
 Laptops2024.07.09Laptop Storage Type Guide (PCIe NVMe, SATA III, HDD, eMMC)
Laptops2024.07.09Laptop Storage Type Guide (PCIe NVMe, SATA III, HDD, eMMC)
-
 Laptops2024.07.02Laptop Storage Speed Comparison (PCie NVMe 5.0, 4.0, 3.0, SATA III)
Laptops2024.07.02Laptop Storage Speed Comparison (PCie NVMe 5.0, 4.0, 3.0, SATA III)
-
 Hardware Guide2024.06.29Desktop Storage vs Laptop Storage Speed Performance Comparison
Hardware Guide2024.06.29Desktop Storage vs Laptop Storage Speed Performance Comparison
-
 Hardware Guide2024.06.23Single-Thread vs Multi-thread CPU For Gaming (List & Benchmarks)
Hardware Guide2024.06.23Single-Thread vs Multi-thread CPU For Gaming (List & Benchmarks)




Hey it’s me Ronald from Zimbabwe. Is was so amazing. Thank you for advise, but i am inspired and motivated by programming and hacking and i sometimes learn on my own. I don’t know if you could help me because being alone in studying computers is to hard for me. My aim was to study cyber security. Will you help me???